BOTTOM LINE UP FRONT (BLUF)
Since the rise and fall of Silk Road, darknet markets (DNMs) have increasingly diversified their offerings from narcotics to sophisticated fraud and cybercrime enablement services. The DNM ecosystem evolves through a repeating cycle of dominance, law enforcement disruption, and subsequent market replacement, leading to an increasingly diversified, highly specialized, and geopolitically concentrated ecosystem. The post-Hydra era has demonstrated a "Cambrian Explosion" of DNMs—an adaptive, resilient criminal ecosystem model capable of rapid reorganisation. 2024 saw just over $2 billion in BTC flow into DNMs (down from $2.7B in 2023). The DNM ecosystem exhibits predictable boom-and-bust market cycles of adaptation following major disruptions, with consistent replacement timelines of 6-12 months following significant takedowns and successor markets typically emerging with enhanced operational security and increasingly specialized service offerings.
Key 2024 Developments:
Dominant Player: Kraken, not to be confused with Kraken Exchange by Payward, Inc., emerged as the dominant platform with ~$737M in revenue (68% YoY growth), displacing Mega Market (whose inflows plunged over 50% YoY).
Market Structure: Wholesale transactions (>$1,000) constitute 71-81% of DNM revenue, indicating sophisticated supply chain operations rather than retail direct to consumer drug sales
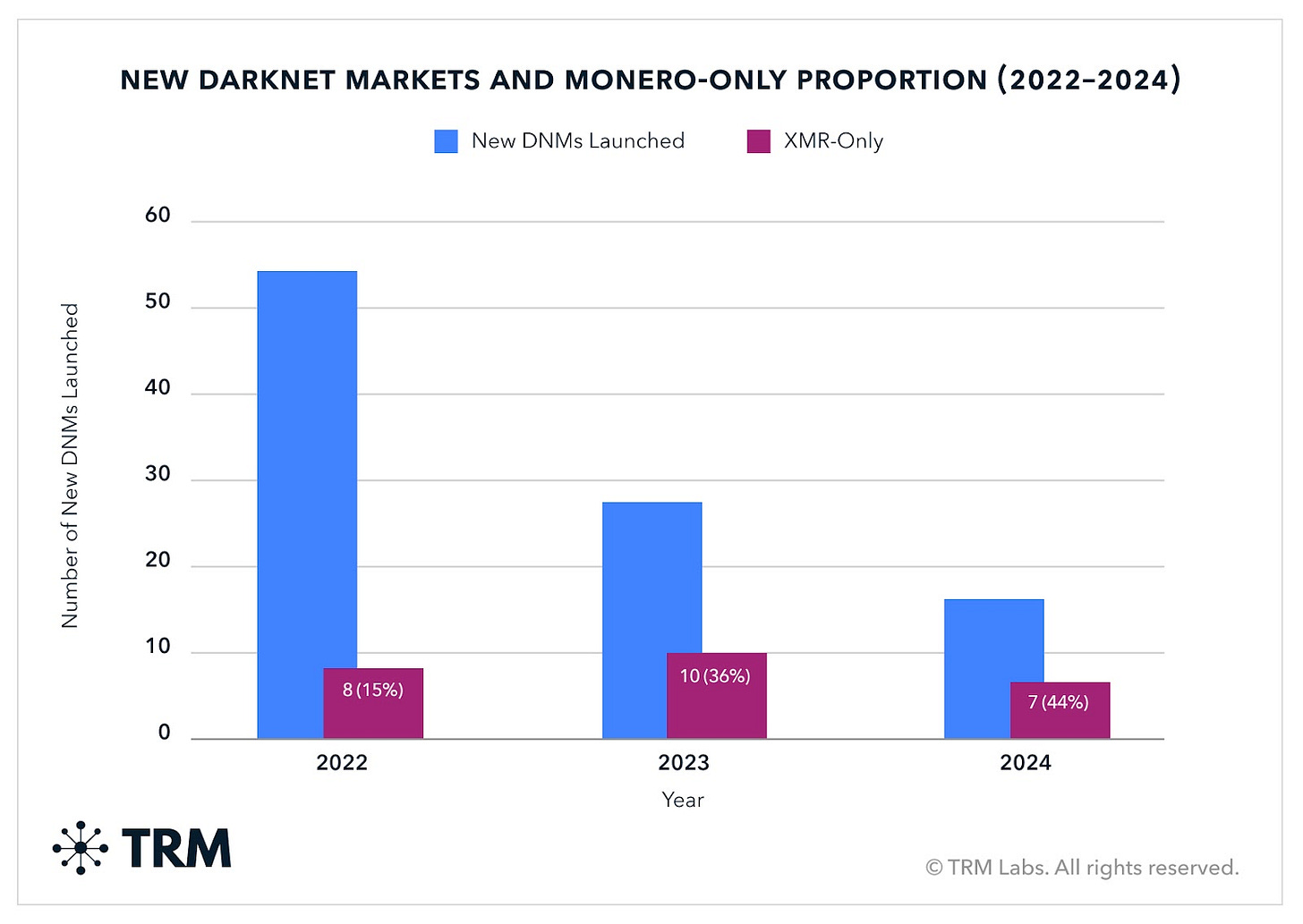
Currency Evolution: Monero adoption accelerated dramatically, with 50% of new DNMs launched in 2024 operating as Monero-only platforms
Specialization: Markets continue to fragment by niche, with cryptocurrency mixers and infrastructure-as-a-service proliferating
Current Ecosystem
Kraken Market (Dominant Russian-Language Platform)
Revenue: $737 million (2024), 68% YoY growth
Market Position: Overtook Mega as leading Russian DNM following aggressive expansion tactics. With Mega Darknet Market showing significant decline (>50% YoY reduction in revenue) and other like BlackSprut seeing modest but substantive revenue decline (-13.6% YoY).
Hostile Takeover: Hacked rival Solaris (January 2025) via GitLab repository compromise, redirecting users to Kraken infrastructure. Market centralization raises cybersecurity and ethical concerns amid ties to Russia-Ukraine conflict. Solaris's SSH keys and AntiDDoS scripts leaked by Ukrainian cybersecurity expert Alex Holden (December 2024)
Innovations: AI-driven dispute resolution, APK distribution via Telegram channels (@KrakenDrugs, @SolarisReloaded), dead drops using "kladmen" system
Geographic Operations: Moscow, St. Petersburg, and occupied Ukrainian cities (Incl. Mariupol and Kherson)
Marketing: Aggressive public advertising including Moscow billboards, traffic-blocking bus (December 2022), hologram displays, and influencer partnerships. Mega used metro ads and influencer Necoglai on Twitch (54,423 viewers), BlackSprut displayed electronic billboards (February 2023)




Western Markets
Abacus Market: $43.3M revenue (183% YoY growth, leading Western platform). Chinese vendors supply PMK (MDMA) and BMK (meth) precursors to 16 DNM vendors globally
Torzon Market: ~$15M estimated market value, 11,000 listings (drugs, counterfeit goods, hacking guides), emphasizes vendor reputation by importing feedback from other markets, offers "premium" account subscriptions
MGM Grand Market: ~$3M revenue (2024), mobile-optimized interface targeting new users with simplified onboarding, 16,000 listings (drugs, fraud tools, stolen financial data), Bitcoin-only payments
WeTheNorth (WTN): Canada-focused market named after Toronto Raptors slogan, 9,000 listings, bilingual (English/French), operates on both clearnet and Tor, enforces strict no-weapons/no-doxxing rules, claims no-logs policy, uses vetting and forum for community trust. Administrator unknown; user "KillDevil" reported in 2022 but not confirmed
Market Specialization
Darknet markets (DNMs) continue to fragment along niche lines, becoming increasingly specialized—separating into categories such as data, drugs, and services. Some now offer “white-label” infrastructure, enabling vendors to launch DNMs with minimal technical expertise. For example, the UAPS network (Sergey Ivanov) processed $1.15B in criminal funds. In contrast, Hydra-style drug markets such as center on drug trafficking find geographic niches, in this case within Eastern Europe. To reduce law enforcement scrutiny, many drug markets now explicitly prohibit the sale of fentanyl and certain high-risk content.
Drug Distribution Networks:
Wholesale Operations: Mega Darknet Market (63.4% share), Kraken (30.9%)
Regional Specialization: Russian markets (Kraken, BlackSprut), Western markets (ASAP 25%, Abacus)
Product Categories: Synthetic opioids, stimulants, psychedelics, precursor chemicals
Infrastructure-as-a-Service Evolution:
Built-in money laundering features like cryptocurrency mixers (e.g Nemesis)
White-label Software providers are proliferating offering turnkey hosting and payment solutions (e.g. iKlad.biz and Klad.cc).
Hacking Enablement Platforms:
Primary Markets: Exploit.in, FreshTools, Cypher Marketplace
Services: Ransomware-as-a-Service, stolen financial data, money laundering infrastructure
Revenue Model: Commission-based, subscription services, direct sales
Financial Fraud and Identity Theft:
Specialized Platforms: BriansClub (credit cards), Russian Market (stolen data), 2easy, BidenCash (promotional dumps)
Service Offerings: Fullz data, CVV shops, RDP access, malware distribution
Vendor Tools Markets: FreshTools, Cypher attract non-drug DNM consumers
Geographic Specialisation:
Russian-language markets dominated global DNM revenue generation, accounting for 97% of the $1.7B in drug-related transactions in 2024. Eastern Europe channels 1.4% of $41B of total crypto volume directed to DNM entities, highest global concentration
Latin America: 1.6% illicit crypto volume (highest globally), less organized DNM structure. Statistically, Latin America became the world’s #2 crypto adoption region by 2024
Western Markets (US/EU): Retail-focused, personal consumption patterns, key platforms include ASAP, Incognito, Abacus
Money Laundering Infrastructure
Exchange Networks:
Garantex Exchange: Sanctioned by OFAC (2022); processed $100M+ for Conti, Hydra, and military procurement ($85M to Chinese UAV manufacturers). Handled $2.6 million in Hydra funds per Treasury sanctions
Monitored Wallets: Tracking garantex-linked wallets
UAPS Network: Sergey Ivanov's exchanges (UAPS, PinPays, PM2BTC) processed over $1.15 billion of criminal funds (ransomware, Hydra, Joker's Stash)
Mixing Services:
Bitcoin Fog: Roman Sterlingov arrested April 2024, charged with laundering ~$336M
Helix Network: Larry Harmon sentenced; successor services continue operating
Tornado Cash: Surprising resurgence despite sanctions
Built-in Mixing: Nemesis Market featured internal mixing capabilities
Recent Seizures:
iKlad.biz: $11M laundered via foreign bank cards (May 2025 Moscow bust)
Qakbot Proceeds: $24M seized from Rustam Gallyamov (May 2025)
Roman Sterlingov (Bitcoin Fog): Arrested April 2024, charged in DC with laundering ~$336M including Silk Road funds, has since pleaded guilty
Larry Harmon (Helix mixer): Sentenced in 2020; newer "Helix successors" continue to circulate
CyberWar Ecosystem
KillNet Operations
Killnet provided DDoS services to Solaris Market in exchange for fees, attacking competitors like RuTor under the guise of “ideological” motives. Killnet’s DDoS campaigns (e.g., U.S. airports, EU Parliament) align with Russian strategic goals, though direct FSB/SVR ties remain unproven.
Hacking Services: Solaris paid $44,000 in BTC to KillNet for DDoS attacks on competitors (RuTor, OMG)
Insider Threat: Infiltrated by Alex Holden (2023), who diverted 1.6 BTC (~$25,000) to Ukrainian charity "Enjoying Life"
Attack Record: 84 confirmed attacks (2022-2024), including EU Parliament, U.S. airports, and Eurovision
Financial Ties: $280,000 donated to Russian military efforts in Ukraine
Fundraising: Raised over $280,000 in cryptocurrency since February 2022, with Chainalysis tracking $2.2 million in donations to 54 groups for Russian military equipment
Conti Ransomware Group
Conti relied on Hydra Market (shut down in April 2022) to procure hacking tools, launder ransomware proceeds, and collaborate with affiliates. Hydra facilitated $1.3B in transactions, with Conti using it to purchase access to compromised networks and leaked credentials. Conti’s leadership, including Vitalii Kovalev (indicted in 2025), operated from Moscow and St. Petersburg, with infrastructure hosted in Russia-friendly jurisdictions like Belarus and Kazakhstan. Conti laundered $180M (2021) via Garantex, a sanctioned crypto exchange linked to Russian military procurement (e.g., $85M to Chinese UAV manufacturers)
Leadership: Vitalii Kovalev (Moscow) linked to $1B in ransomware proceeds; indicted by U.S. DoJ (May 2025)
Infrastructure: Used Qakbot malware (developed by Rustam Gallyamov) to extort $25M from U.S. victims (2021)
DNM Integration: Utilized Hydra Market infrastructure for money laundering operations


Financial Flows
Transaction Pattern Analysis:
Retail drug customers (sub-$100 purchases) now contribute a minority of DNM revenue; wholesale purchases (>$1,000) drove 71–81% of darknet drug sales in 2024.
Wholesale purchases (>$1,000): 71-81% of total revenue
Large retail ($100-$500): 35.7% of transaction volume
Social supply ($500-$1,000): 37.1% of transaction volume
Small retail (<$100): 16.5% of transaction volume
Privacy Coin Adoption
We’re witnessing a relative decline in Bitcoin usage relative to more privacy focused ledgers.
Monero (XMR) Dominance: 95% of Russian DNM drug sales ($1.4B in 2023) shifted to XMR to evade blockchain tracing
New Platform Adoption: 50% of new DNMs launched in 2024 operate as Monero-only platforms
Transaction Share: XMR transactions constitute 42% of total DNM activity (2024)
Enhanced Privacy: Other privacy coin usage (Zcash) driven by enhanced blockchain analysis capabilities
Operational Security
Dead Drop System (Zakladka)
Geographic Spread: 2,000+ locations in Russia (Moscow, Siberia) and occupied Ukraine
Methods: Items buried in ground, attached by magnets to lamp-posts, or taped underneath window sills
Enforcement: Couriers punished via filmed beatings/sexual assaults/murders on Telegram; $180 bounties for failed drops
Revenue Model: Kladmen (couriers) system generates revenue through physical distribution networks
Technical Security Measures
Encryption: PGP encryption standard across platforms (Kingdom Market admin used official PGP key to announce "The kingdom has fallen" during takeover)
Access: Tor-only access with no-logging policies
Communication: Encrypted messaging via Telegram
Payment Security: Self-custody emphasis, DEX usage, privacy coin integration
Infrastructure: Zero-logging VPS services, API-based crypto processors
Vendor Operations: Strong OPSEC including invite-only forums, PGP-encrypted messaging between users
Global Precursor Supply Chains
Chinese Vendors: Supply PMK (MDMA) and BMK (meth) to 16 DNM identified vendors globally via Abacus Market
OFAC Connections: One vendor tied to designated traffickers Alex Peijnenburg and Matthew Grimm ($1.5M in sales)
Novel Synthetics: Nitazenes are 20x stronger than fentanyl; distributed via counterfeit M30 pills. Many new synthetics are sourced from Chinese labs (e.g., identified protonitazene vendor in Shanghai area and Guangzhou facilities linked to Abacus Market).
Case Studies:
Silk Road (2011-2013)
Operator: Ross Ulbricht (alias "Dread Pirate Roberts") Scale: $183M+ in transactions, controlled 20% of Bitcoin economy at peak Compromise Methods:
Posted personal Gmail (rossulbricht@gmail.com) in Bitcointalk advertisement
Server IP misconfiguration revealing Iceland address (193.107.86.49)
VPN dropouts exposing San Francisco café logins near Hickory Street residence
Ideological post correlation across platforms
Pen register on Ulbricht's Comcast account
Investigation:
Insider Threat: DEA infiltrator deployed as site administrator; 60+ controlled purchases across 10+ countries (November 2011-September 2013)
Technical Exploitation: Icelandic police seizure of Thor datacenter server (complete hard drive mirror), SSH log analysis revealing non-Tor administrative connections from Philadelphia, France, and Romania
Digital Forensics: Tom Kiernan conducted 3-hour real-time RAM and disk imaging to confirm data integrity
International Cooperation: FBI, DEA, IRS, NYPD, ICE-HSI, ATF, Secret Service, Marshals, Australian Federal Police, Irish Computer Crime Investigation Unit, Reykjavik Metropolitan Police, French Central Office for Fight Against CyberCrime
Blockchain Analysis: Traced 174,000 BTC in proceeds
Arrest: October 1, 2013, Glen Park Library with unlocked Samsung 700z laptop showing admin console, DPR's PGP private key, chat logs, financial spreadsheets (2011-2013), and administrative backdoor evidence
Sentence: Life without parole (May 29, 2015)
AlphaBay (2014-2017)
Operator: Alexandre Cazes (Canadian, aliases "Alpha02," "Admin") Scale: 200,000+ users, $450M in deposits, 4M BTC transactions Compromise Methods:
Used "Pimp_Alex_91@hotmail.com" for automated site emails and password resets
Misconfigured forum registration (2014) exposing Netherlands server IP through email headers retained by FBI source
Reused "Pimp_Alex_91" across platforms including French social network Skyrock.com with personal photos and birth year (1991)
Operated EBX Technologies web hosting company under real name
Technical Operations:
Coordinated Cyber-Physical: BKA remotely induced service outage forcing Cazes to log back in, capturing live admin session
Digital Forensics: Complete hard drive image containing database dumps, GPG keyrings, Bitcoin wallet files, server access logs, escrow passwords, evidence of luxury purchases (Lamborghini) funded by darknet profits
Blockchain Analysis: Chainalysis Reactor and demixing algorithms traced flows through site mixers, identifying cash-out points and flagged wallet addresses
International Cooperation: FBI, DEA, U.S. Postal Inspection, Europol, Thai police, partners in Canada, Netherlands, Lithuania, France
Identification Pathway: leaked welcome email → "Pimp_Alex_91" correlation → social media profiles → programming forum posts with full name signature → LinkedIn/hosting company verification → financial records matching civil forfeiture assets
Takedown: July 2017 coordinated operation, Cazes found dead in Thai custody, 60% temporary drop in darknet activity
Hydra Market (2015-2022)
Operator: Dmitry Olegovich Pavlov (Promservice Ltd) Scale: $5.2B in cryptocurrency processed, 80% of DNM crypto volume by 2021 Investigation Methods:
18-month Joint Operation: German BKA coordinated with FBI, DEA, IRS-CI, U.S. Postal Inspection (August 2021-April 2022)
Technical Exploitation: Darknet monitoring to identify German hosting providers, judicial takedown orders, complete server imaging, database reverse-engineering revealing user ledgers, escrow balances, vendor lists, internal mixer wallet structures
Intelligence Operations: Embedded law enforcement agents posing as vendors/buyers, behavioral profiling through UTC offset timing and language analysis, vendor clustering, intelligence-sharing through EUROPOL's SSD and FBI's JCODE
Digital Forensics: User account databases, chat logs, transaction histories, PGP key cryptographic analysis, UTXO de-mixing analysis, admin access logs showing IP connections to Pavlov's hosting company, hash-verified physical media under chain-of-custody protocols
Identification Pathway: Administrative company records (Promservice/All Wheel Drive) linking Pavlov to server infrastructure, Treasury sanction documentation of 49 wallet addresses, public company filing analysis, cross-analysis of IP logs with corporate infrastructure
Seizures: 543 BTC (~$25M), complete server databases Sanctions: U.S. Treasury simultaneously sanctioned Hydra's exchange connections Revenue Scale: $1.3 billion (2020), facilitated $8 million in ransomware proceeds (Ryuk, Sodinokibi, Conti) Aftermath: Stanislav Moiseyev sentenced to life (December 2024); 15 accomplices received 8-23 years. Pavlov indicted by U.S. Justice Department but remains at large
Conclusions:
The darknet marketplace ecosystem has demonstrated remarkable resilience and adaptability over its 14-year evolution. The transformation from Silk Road's monolithic structure to today's specialized, geographically concentrated network of increasingly diversifies and offerings from narcotics to sophisticated fraud, cybercrime enablement and logistical support for grayzone conflicts. The DNM ecosystem will continue to evolve through a repeating cycle of dominance, law enforcement disruption, and subsequent market replacement. The connection between DNM profits and military procurement activities demonstrates the national security implications of the ecosystem.
Ecosystem Resilience: The DNM ecosystem's ability to rapidly reconstitute following major disruptions indicates that traditional takedown approaches may have limited long-term effectiveness without addressing underlying infrastructure dependencies.
Geographic Concentration: The dominance of Russian-language markets, generating 97% of global DNM drug revenue, presents both challenges and opportunities for law enforcement targeting strategies.
Operational Sophistication: The rapid adoption of privacy coins, DeFi platforms, and sophisticated operational security measures suggests that technical capabilities must evolve to maintain investigative effectiveness. The shift to Monero-only platforms represents a significant intelligence gap requiring enhanced blockchain analysis capabilities.
Niche Specialisation: The increasing integration of DNM infrastructure with ransomware operations, cybercrime services, and traditional organized crime networks represents a fundamental threat to global security and economic stability.
End of Brief
[For more information on Section 14 please click here.]